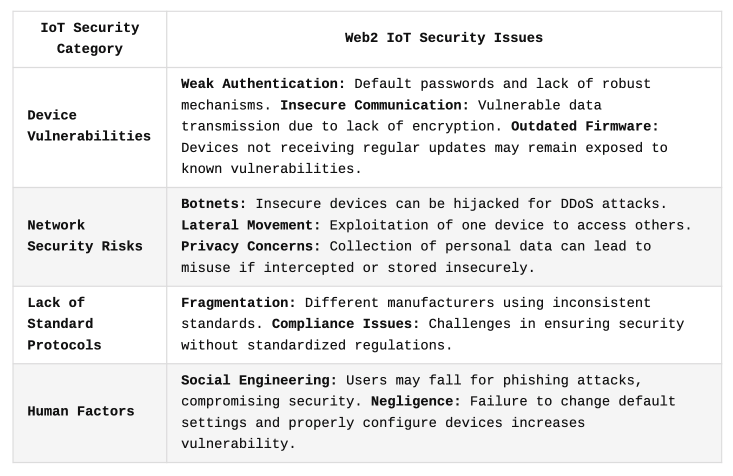
NoSec Cybersecurity Consulting knows that Web2 IoT devices are prone to hardware attacks, at the source, but even worse they are prone to digital twin and device clones which replicate traffic and identities of devices in real-time.
The current setup of IoT within typical TCP/IP models for IoT deployments fails the cybersecurity, availability, and integrity of IoT devices and therefore all data of Web2 IoT producers/consumers alike.
The integrity of IoT software requires better technical deployments, that leads us to Web3 IoT.
NoSec Cybersecurity Consulting seeks these answers to improve shadow IoT and IoT cybersecurity issues such as with Nano-IoT, 6G, and many more concerns for future cybersecurity impacts of IoT on humanity.