From a strategic perspective, a Zero Trust Architecture has replaced perimeter security, and on the tactical level, Zero Trust is all about Identity. Zero Trust in Web2 is only partially implemented ideally. In Web3, Zero Trust takes it to another level of secure implementation.
Web2 is based on a legacy ‘centralized server-client model’.
Web3 ideally is based on the reverse of this legacy model.
The typical Web2 tech stack includes:
* Servers: Operating systems like Linux, web servers such as Apache/Nginx, and databases like MySQL/PostgreSQL.
* Client: Web interfaces built with HTML, CSS, and JavaScript.
* Communication protocols: HTTP/HTTPS request-response model.
* Cloud Infrastructure: AWS, Google Cloud, Azure, and similar services.
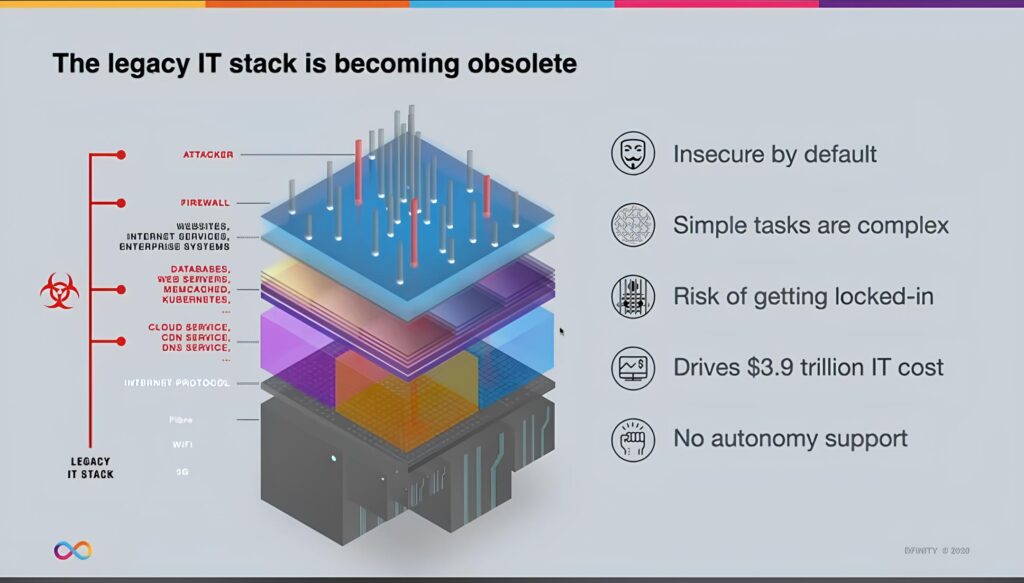
Source: internetcomputer.org
The Web3 tech stack consists of:
* Infrastructure: Blockchain networks (Ethereum, Solana, etc.).
* Smart Contracts: Decentralized application logic written in Solidity.
* Distributed Storage: Content storage systems like IPFS and Arweave.
* Client Interfaces: Libraries such as Web3.js and Ethers.js for blockchain interactions.
* Wallets: Private key management tools like MetaMask.
Source: wepin.io/en/blog/web2-vs-web3-architecture
Zero Trust is one of the top cyber security trends this decade, with more and more organizations adopting micro-segmentation, user context checks, perimeter-less, automated security consensus, and continuous session monitoring.